
Monitor365 helps to protect your M365, the most attacked business service in the world.
Most companies use Microsoft 365 cloud services to benefit from the improved availability, features and convenience. The popularity and accessibility has also made Microsoft 365 one of the most targeted environments by threat actors. Attackers employ a variety of techniques to guess or steal user credentials.
Compromised Microsoft 365 accounts are the most common security incident we assist clients with. In many cases, the initial indications come after the damage has already been done and post-mortem investigations usually find early signs of an account compromise, that went unnoticed.
This is where we can help!
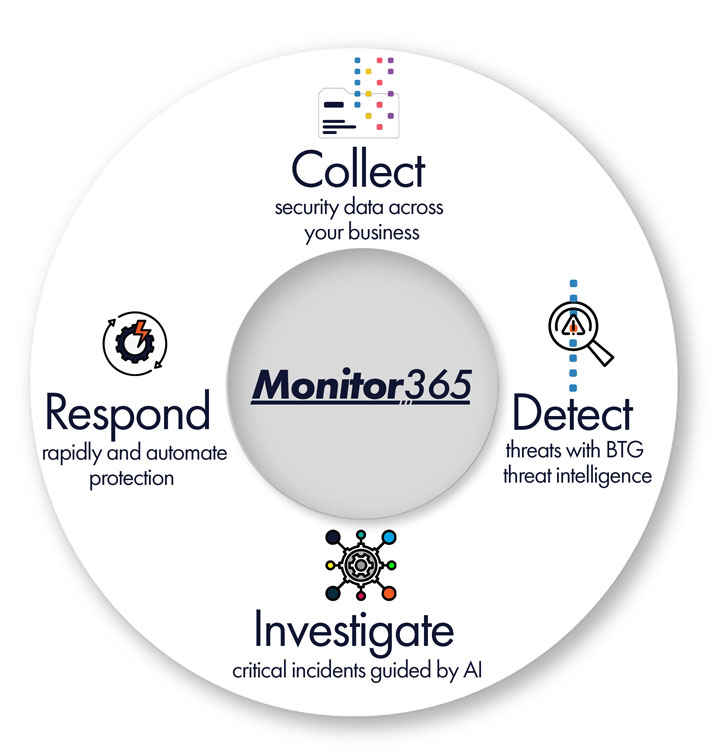
Monitor365 is BTG’s monthly service that can help you by providing monitoring, proactive triage and notifications of suspicious activity. We integrate our logging and analysis platform with your Microsoft 365 tenancy to retrieve and analyse key event logs. We monitor your environment to establish a baseline of normal activity. This helps us identify unusual events and then respond to generated alerts. We research events, correlating activity and data from multiple sources, to assess whether an event is suspicious or not.
Simple Monthly Billing
Per user, per month billing for your organisation.
 Some of the biggest risks M365 customers face, include:
Some of the biggest risks M365 customers face, include:
- Phishing scams and malware sent to external parties, damaging your company reputation.
- Fraudulent attacks targeting you and external partners, resulting in financial losses and reputational harm.
- Sensitive company data stolen through Exchange, SharePoint or OneDrive.
- Theft of external client, supplier and partner details that can be used by attackers.
Microsoft provides some excellent tools to help secure and protect businesses, including conditional access policies and multi-factor authentication (MFA).
However, these measures are not guaranteed to prevent attacks.
As more businesses implement controls like MFA, attackers are becoming more adept at working around them. Password exposure can also place other company resources at risk of unauthorised access. Conditional access and MFA can help identify these cases by showing when access was blocked, but a valid password was used. However, it is necessary to monitor for this activity in order to identify and respond to it.
It is important to continually monitor your event logs for suspicious activity and respond before the damage is done.
Our managed service includes regular review of Microsoft 365 security alerts and sign-in activity, allowing us to detect patterns of concern early. We notify clients about suspicious activity requiring action and assist with any requested response activities—helping to reduce risk, limit exposure, and keep your environment secure. Continuous visibility and proactive response are critical to staying one step ahead of today’s threats.
We see regular attacks launched against our clients’ Microsoft 365 services and have developed specialised knowledge to understand how to interpret the M365 event logs and detect attacker activity. Our proven service has helped clients identify many compromised accounts and take corrective actions before any harm is done, saving them from expensive incident response activities, as well as potential reputational and financial harm.
MONITOR365 FEATURES
- A cost effective way to provide effective security monitoring of one of the highest-risk areas.
- Monitoring of your Microsoft 365 logs for suspicious activity and alerts, regardless of your current Microsoft 365 licensing tier.
- Integrated threat intelligence and client-specific, custom alert logic.
- Monitoring for unusual activity based on typical company activity.
- Initial triage and investigation of suspicious events.
- Notification of detections requiring further investigation or remedial activities.
- Longer retention of key Microsoft 365 activity logs for historic investigation and additional context.






