Enable Secure access without exposing your network
 Organisations are seeking a safer and user-friendly way to enable remote work, as traditional network-centric solutions like VPNs and firewalls are vulnerable to attacks.
Organisations are seeking a safer and user-friendly way to enable remote work, as traditional network-centric solutions like VPNs and firewalls are vulnerable to attacks.
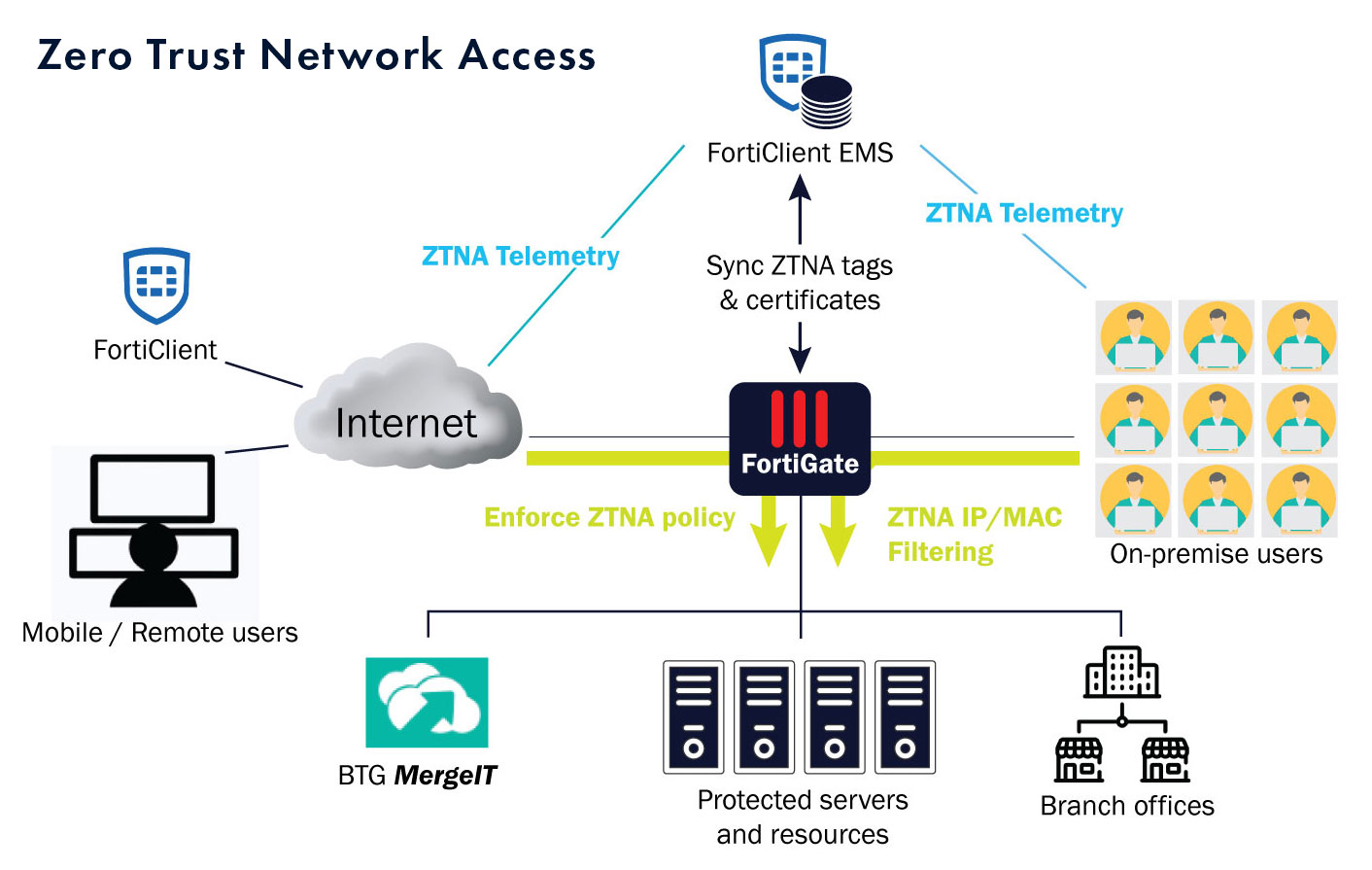
The solution lies in implementing zero trust principles for application access through Zero Trust Network Access (ZTNA). This approach continuously verifies user and device identities and only grants access to necessary applications, improving security and user experience.
Fortinet’s ZTNA feature requires a FortiGate device and the FortiClient endpoint agent, providing secure access for both remote and on-premise users with polices enforced at FortiGate. The system verifies various factors to ensure secure access and employs top-tier security systems for threat protection.
Features
Flexible deployment
Deploy ZTNA in various ways whether hosted in BTG’s comprehensive IaaS cloud platform, MergeIT or in the data centre, public cloud (e.g., AWS, Azure), private cloud, hybrid solution, or a SaaS application (e.g., Microsoft 365, Salesforce.com) catering to organisations of all sizes.
Ongoing verification
Continuously verify user and device identities to prevent unauthorised access to applications, even after initial access has been granted.
Granular access control
Provide granular control over application access, allowing organisations to define who has access to specific applications, reducing the risk of unauthorised access to sensitive data.
Context-aware security
Make security decisions based on factors like user identity, device posture, and network location, providing access only when necessary.
Integrated security
Combine ZTNA with Fortinet’s other security solutions, such as firewalls and intrusion detection systems, for comprehensive application and data protection against various threats.
Key Benefits
Improve Security
Improve security posture by reducing the attack surface, preventing unauthorised access and minimising the risk of breaches.
Reduced Complexity
The solution simplifies network security management by offering a unified platform for access control.
Enhance User Experience
Simple and seamless experience when accessing applications as the solution does not require users to install or configure any additional software.
Scalability
Suitable for businesses of all sizes.
Reduce Costs
Help businesses reduce security costs by eliminating the need for expensive VPN hardware and software.
Improved Agility
Quickly deploy and manage new applications and services in the cloud.
FAQ
What is the concept of Zero Trust?
Zero Trust is a modern cybersecurity model based on a simple principle: “never trust, always verify.”
Instead of assuming everything inside your network is safe, Zero Trust treats every user, device, and application—inside or outside—as potentially compromised. Access is only granted when identity, context, and risk have been verified.
Core concepts:
Verify explicitly – Always authenticate and authorise based on all available data points (user identity, device, location, etc.).
Least privilege access – Users get only the access they need, no more.
Assume breach – Continuously monitor, log, and respond as if a threat may already exist.
It’s a proactive, layered approach to reducing risk—especially in hybrid work environments where traditional perimeters no longer apply.
What is the Zero Trust technique?
The Zero Trust technique is a cybersecurity approach that enforces strict identity verification and access controls—no one is trusted by default, even inside your network.
Key techniques include:
Multi-Factor Authentication (MFA): Confirm user identity with more than just a password.
Micro-Segmentation: Break the network into small zones to limit lateral movement.
Least Privilege Access: Give users the minimum access needed for their role.
Continuous Monitoring: Constantly assess user behaviour and device health.
Device Compliance Checks: Only allow access from verified, secure devices.
Policy-Based Access: Decisions based on context like user role, location, and risk level.
Together, these techniques help protect against threats, contain breaches, and secure data—whether on-prem, in the cloud, or remote.
What are the three principles of Zero Trust?
The three core principles of Zero Trust are:
1. Verify Explicitly
Always authenticate and authorise based on all available signals—user identity, device health, location, role, and more. Trust nothing by default.
2. Use Least Privilege Access
Limit access to only what users or systems need to perform their tasks. This reduces risk if credentials are compromised.
3. Assume Breach
Operate as if an attacker is already inside. Monitor continuously, segment access, and respond quickly to anomalies.
These principles form the foundation of a proactive, adaptive cybersecurity strategy that protects against modern threats.
What are the 5 pillars of Zero Trust?
The 5 pillars of Zero Trust represent core areas where Zero Trust principles must be applied:
1. Identity
Verify every user and service account. Use strong authentication (e.g. MFA), role-based access, and continuous validation.
2. Device
Only allow secure, compliant devices to access resources. Monitor device health and manage risk in real-time.
3. Network
Segment the network and enforce strict access controls. Encrypt traffic and monitor all activity—inside and out.
4. Application Workload
Secure access to applications based on context. Protect workloads across cloud, on-prem, and hybrid environments.
5. Data
Protect data at rest, in transit, and in use. Classify, encrypt, and restrict access based on sensitivity and user needs.
Together, these pillars help build a resilient, adaptive security posture based on continuous verification—not assumptions.
